Enhancing IT security compliance with DevOps and Infrastructure as Code
Introduction
In today's fast-paced digital landscape, ensuring IT security compliance is more critical than ever. With cyber threats evolving rapidly, organizations need solutions that allow them to maintain strict control over security while minimizing the possibility of downtime and breaches. One promising strategy is to integrate DevOps practices with IT security compliance efforts.
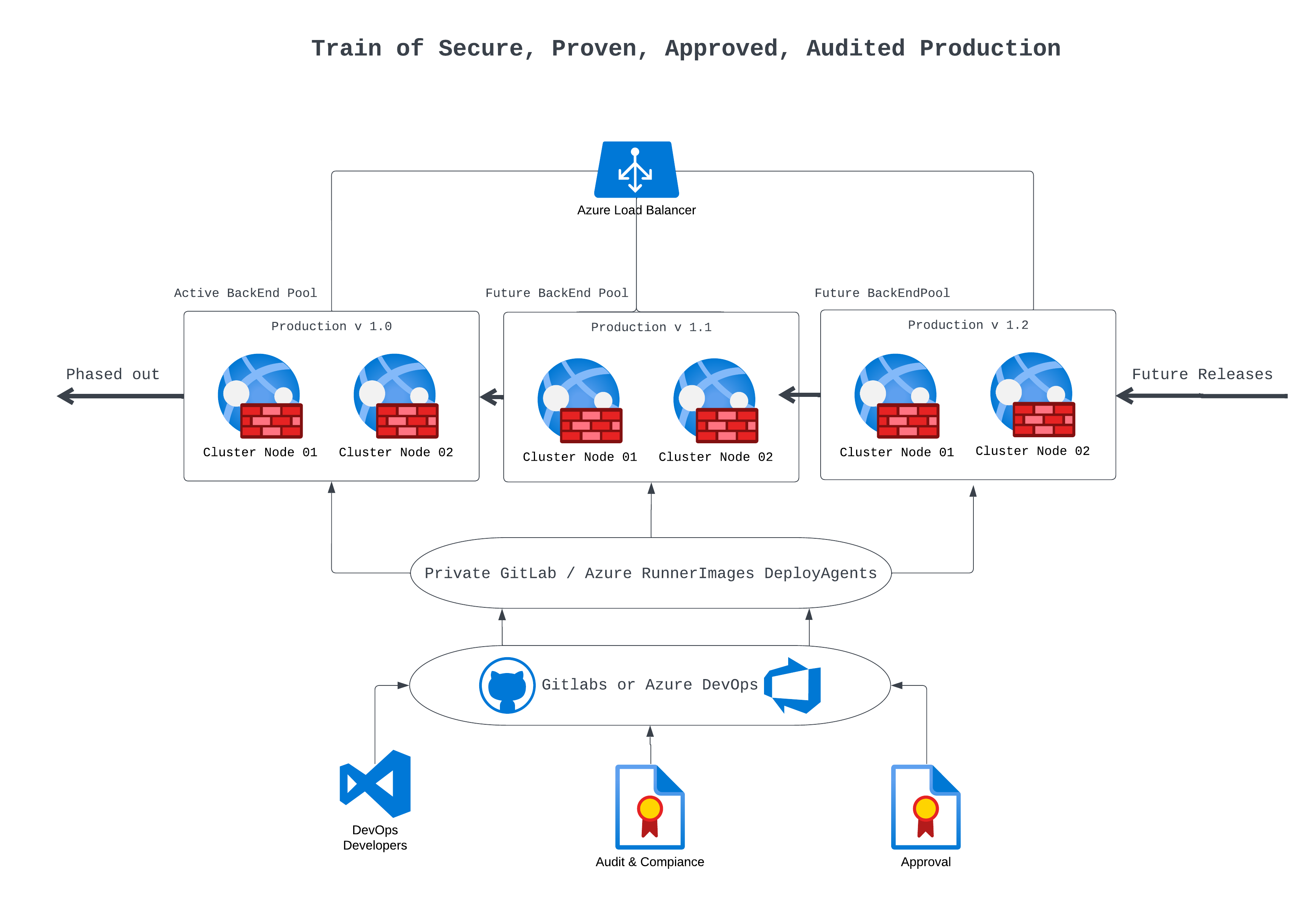
This approach leverages tools like: Terraform , Bicep or Ansible to create, manage, and redeploy internet facing hosts that are secure and auditable.
The role of repeatability and auditing in security compliance
Repeatability is at the heart of secure and compliant IT operations. When systems can be reliably reproduced using consistent configurations and automation scripts, auditing becomes a systematic process rather than a reactive measure. By ensuring each deployment meets stringent security standards, organizations can quickly identify deviations from compliant setups. This proactive approach transforms auditing into a continuous tool for security improvement.
How DevOps practices answer these challenges
DevOps emphasizes speed, consistency, and automation. Integrating security compliance with DevOps practices offers several key benefits:
- Infrastructure as Code (IaC) for Consistency:
Using tools like Terraform, Bicep, and Ansible, every internet-facing host is built from precise, pre-defined configurations. This method ensures that security controls such as firewall rules, encryption protocols, and access permissions are uniformly applied. It also simplifies the auditing process, as compliance can be verified against the exact configuration used for deployment. - Rapid Redeployment to Minimize Downtime:
In the event of a security breach, the ability to redeploy infrastructure rapidly is invaluable. DevOps practices empower teams to replace compromised hosts within minutes rather than hours or days. This swift response minimizes downtime and reduces the window of opportunity for attackers. - Risk Reduction Through Regular Redeployment:
Regularly redeploying hosts provides a proactive strategy to eliminate lingering threats left by intruders. By scheduling deployments at desired intervals, organizations can ensure that their systems remain fresh and secure, preventing malicious actors from maintaining a persistent presence.
Benefits of integrating DevOps and IaC
in IT security compliance
- Consistent enforcement of security policies
Every host built via IaC minimizes configuration drift, ensuring that security policies are applied uniformly and that systems reflect the latest compliance standards. - Enhanced auditing capabilities
Automated deployments leave clear audit trails that streamline vulnerability identification and remediation. This documentation is invaluable during regulatory reviews. - Increased agility in incident response
Rapid redeployment minimizes disruption and exposure during a security incident, allowing organizations to respond swiftly and confidently. - A Proactive security posture
Regularly rotating hosts and updating configurations help prevent attackers from establishing long term footholds, shifting the focus from reactive measures to proactive threat mitigation.
Conclusion
Integrating DevOps practices with IT security compliance represents a transformative shift in how organizations approach cybersecurity. By leveraging Infrastructure as Code with tools like Terraform, Bicep, and Ansible, repeatability and auditing become an integral part of modern IT operations. This not only ensures continuous adherence to security standards but also enhances incident response capabilities and reduces overall risk.
Embracing this DevOps driven methodology empowers companies to build a resilient and agile IT environment. As cyber threats continue to evolve, adopting these best practices will be essential for securing digital assets and maintaining a robust compliance posture.