Phased Implementation of Zero Trust: Prioritizing Pre-Authentication for Applications and APIs
In the evolving landscape of cybersecurity, Zero Trust has emerged as a critical framework for organizations seeking to protect their digital assets. However, implementing a comprehensive Zero Trust architecture can be overwhelming, expensive, and fraught with technical challenges. This article proposes a more practical approach: a phased implementation that prioritizes pre-authentication for applications and APIs—the primary targets for most threat actors.
Understanding Attacker Priorities
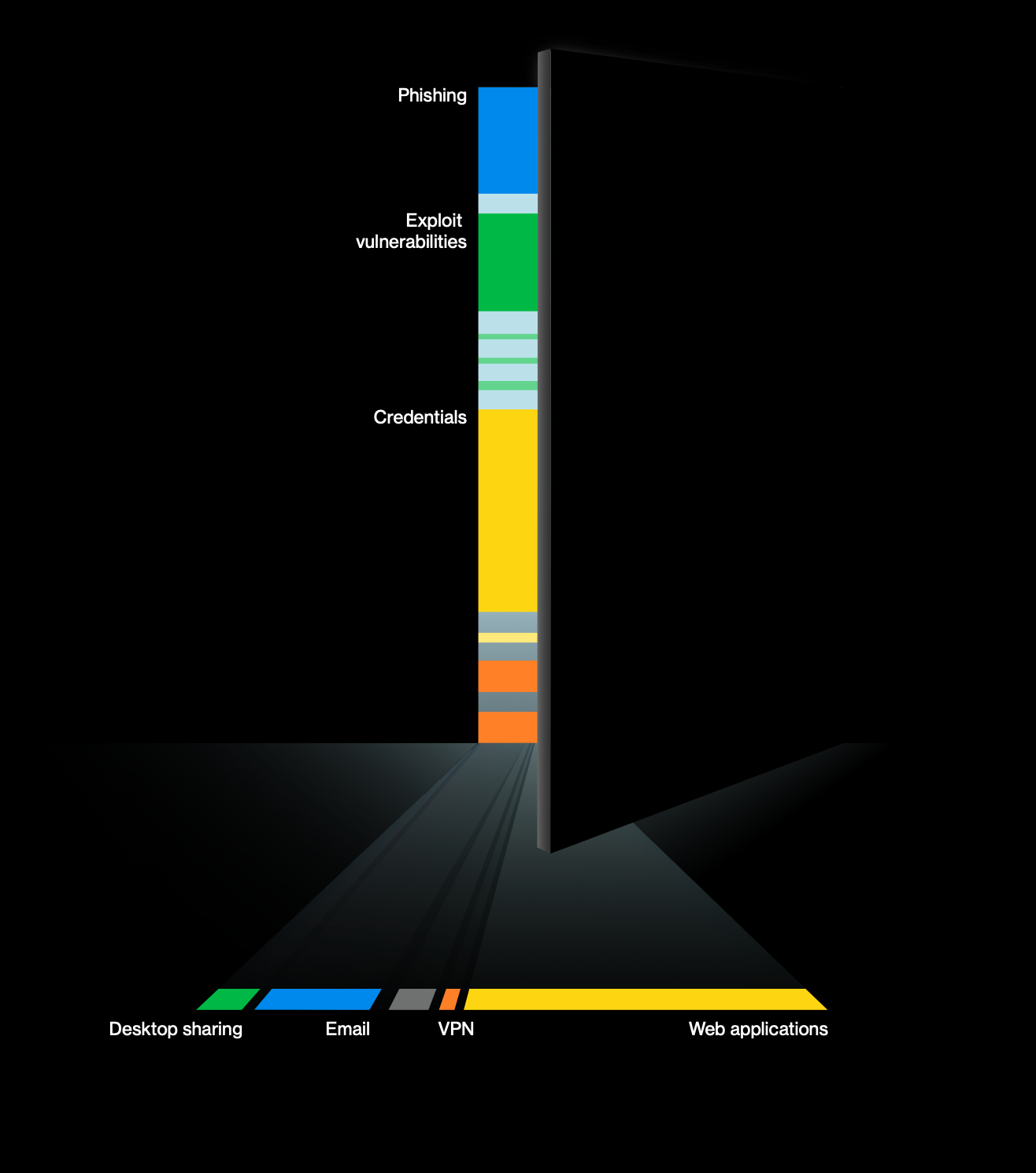
To effectively implement Zero Trust principles, we must first understand where attackers focus their efforts. Data from multiple security reports consistently shows that:
- Applications and APIs are primary targets : Between 40% - 60% of successful breaches begin with attacks against web applications or APIs
and 70% of the successful breaches are done by attacking servers not clients - Credential abuse is prevalent: Compromised credentials are involved in approximately 60% of breaches.
- Unauthenticated access is exploited: Attackers frequently target resources that lack strong authentication controls
«The biggest shift seen in networking and security over the past 24 months has been that work is no longer a place we go to but rather an activity we perform. Hybrid work is our new normal, which means our apps and users are now everywhere and anywhere, dramatically increasing our attack surface. In parallel, we’ve also seen an increase in the sophistication and volume of cyberattacks attempting to take advantage of this massively increased attack surface.» -Palo Alto Networks
By understanding these threat patterns, we can strategically prioritize our Zero Trust implementation to address the most likely attack vectors first. Implementing pre-authentication requirements for all services will create a robust software-defined perimeter, significantly reducing our overall attack surface. Enabeling pre authentication on all services is what ZTNA 2.0 is all about.
The Case for Phased Implementation
Rather than attempting to implement a comprehensive Zero Trust architecture all at once, an approach that often leads to project delays, budget overruns, and technical complications, organizations should consider a phased approach that delivers incremental security improvements:
Benefits of Phased Implementation
- Faster time to value: Security improvements begin much sooner
- Lower initial investment: Resources can be allocated more efficiently
- Reduced complexity: Teams can focus on mastering one component at a time
- Easier user adaptation: Changes can be introduced gradually
- Better risk reduction per dollar: Initial investments target the most critical vulnerabilities
Recommended Phasing Strategy
A practical phased approach to Zero Trust should begin with securing the most vulnerable and valuable assets—applications and APIs—through strong pre-authentication mechanisms.
Pre-Authentication gives ZTNA
Pre-authentication represents one of the most effective initial steps in a Zero Trust journey providing us with Zero Trust Network Access 2.0 (ZTNA2.0).
By implementing authentication before allowing access to applications and APIs, organizations can:
- Create a security boundary: Establish a clear perimeter where authentication decisions are made on a per application or API basis
- Reduce attack surface: Prevent unauthenticated traffic from reaching application code
- Centralize access control: Implement consistent authentication policies across multiple resources
- Enable detailed access logging: Gain visibility into all authentication attempts
- Separate security from application logic: Remove burden of beeing directly internet exposed from application developers
How Pre-Authentication Embodies Zero Trust Principles
Pre-authentication directly implements several core Zero Trust principles:
- "Never trust, always verify": Every request must be authenticated before accessing resources
- Least privilege access: Authentication can be tied to specific resource permissions
- Assume breach: By authenticating each request, damage from compromised network segments is limited
- Explicit verification: Identity is verified explicitly rather than assumed based on network location
Implementation Approaches for Pre-Authentication
Reverse Proxy Pre-Authentication
A reverse proxy with pre-authentication capabilities offers an efficient starting point:
- Deploy a reverse proxy in front of applications and APIs
- Implement authentication mechanisms appropriate for your environment (OIDC, SAML, etc.)
- Configure access policies based on user identity and request characteristics
- Establish monitoring and logging to track authentication events
This approach can be implemented without modifying existing applications, making it an ideal first phase in a Zero Trust journey.
API Gateway Authentication
For organizations with significant API footprints:
- Deploy an API gateway as the entry point for all API traffic
- Implement token-based authentication (JWT, OAuth 2.0)
- Define fine-grained access controls at the API operation level
- Monitor API usage patterns to detect anomalies
Identity-Aware Proxies
Cloud providers offer identity-aware proxy services that can:
- Authenticate users before allowing access to applications
- Apply context-aware access policies based on user, device, and request attributes
- Provide detailed access logs for security analysis
- Integrate with existing identity providers for consistent authentication
Measuring Success
Effective metrics for evaluating your pre-authentication implementation include:
- Reduction in authentication-based attacks
- Decrease in successful application/API exploitation
- Improved detection of credential abuse attempts
- Increased visibility into access patterns
- Reduced time to respond to suspicious authentication events
Planning Your Phased Implementation
Step 1: Asset Inventory and Prioritization
Begin by:
- Identifying your most critical applications and APIs
- Determining which resources contain sensitive data
- Assessing current authentication mechanisms
- Prioritizing resources based on risk and value
Step 2: Select Initial Pre-Authentication Mechanism
Choose an approach that:
- Integrates with your existing identity infrastructure
- Scales to your application/API footprint
- Provides comprehensive logging and monitoring
- Minimizes impact on user experience
Step 3: Implementation and Validation
During implementation:
- Start with less critical applications to refine the approach
- Validate that authentication policies work as intended
- Establish monitoring for authentication events
- Create incident response procedures for authentication failures
Step 4: Expansion and Enhancement
After initial success:
- Extend pre-authentication to additional resources
- Implement more sophisticated policies based on context
- Integrate with additional security controls
- Begin planning subsequent Zero Trust phases
Conclusion
A phased approach to Zero Trust that begins with pre-authentication for applications and APIs delivers significant security benefits while avoiding the pitfalls of attempting a comprehensive implementation all at once. By focusing first on how attackers actually target your organization—primarily through applications and APIs—you can achieve the greatest risk reduction for your investment.
Pre-authentication embodies core Zero Trust principles and creates a foundation upon which additional security controls can be built. Organizations that take this pragmatic approach will find themselves better protected against the most common attack vectors while positioning themselves for continued security maturation.
Remember that Zero Trust is a journey, not a destination. By starting with pre-authentication and building outward, organizations can make that journey more manageable, more cost-effective, and ultimately more successful in protecting their digital assets from increasingly sophisticated threats.
I Have also written an article where i describe how i have successfully implemented what is described in general terms in this article using Azure Services
"A phased implementation of Zero Trust using Azure services"